Recently, We reported about the Reflected Cross Site scripting vulnerability in the HostGator India hosting site that affects millions of hosted sites. Today, Another Indian Security Researcher , Ramneek Sidhu , come with another interesting find.
Ramneek Sidhu has discovered Reflected XSS Vulnerability in One of the Biggest WebHosting site "HostMonster" (hostmonster.com). Just like in the previous case, this Vulnerability affects all sites hosted in the HostMonster.
The vulnerability discovered in Subdomain of Hostmonster:http://host104.hostmonster.com/"><SCRIPT>alert(document.cookie)</SCRIPT><SCRIPT>alert("Evolution of Revolution")</script><img src="http://i49.tinypic.com/1zq7cyp.jpg /" />
The vulnerability was reported to Aarshit Mittal by the Security Researcher. Aarshit started to analyze the vulnerability and find few more
interesting things. He discovered that each and every websites hosted in the Hostmonster vulnerable to Reflected XSS.
Find the list of sites hosted in Hostmonster. You can do this by searching for "Ip:ip:74.220.207.104" in Bing. This single IP search gives 36,000 results. All of those sites are affected by this security flaw. For instance, let us take "vividhbharti.com".
The POC for this site is:http://vividhbharti.com/"><SCRIPT>alert(document.cookie)</SCRIPT><SCRIPT>alert("Evolution of Revolution")</script><img src="http://i49.tinypic.com/1zq7cyp.jpg /" />
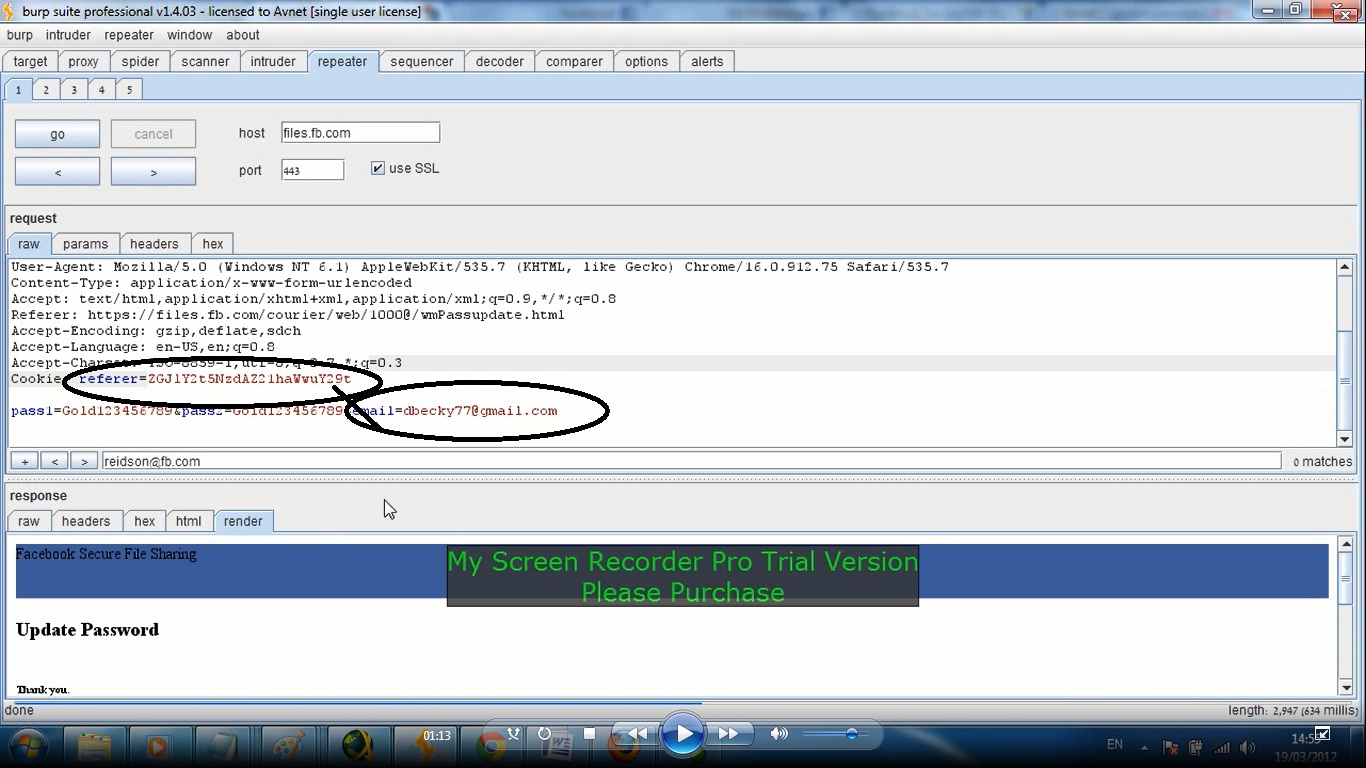
At EHN, i have just Analyzed the affected sites to know what cause this security flaw. It seems like this flaw occured when the developer try to display the ads in the 404 not found page.
There is a javascript code that generate ads. Interestingly, the code uses referrer . The referrer is the current address. Unfortunately, the developers fails to sanitize the url. This results in Reflected XSS.